Всем понятно что это удобно, особенно когда бух не знает как набрать фамилию свою на английском =).
В инете достаточно инфы по этому поводу, но все таки хотел написать
подробнее как это все делается, как оказалось все очень просто.
Инфа:
OpenLDAP
– бесплатный сервер каталогов, который содержится в большинстве
дистрибутивов Linux и FreeBSD. Он обладает достаточной
функциональностью и полностью совместим с Outlook Express, Mozilla и
Mozilla Thunderbird.
Устанавливаем Apache, PHP и модули PHP, не забываем про php5-ldap
Установка OpenLDAP клиента
//> cd /usr/ports/net/openldap23-client/
/usr/ports/net/openldap23-client/> make install clean
/usr/ports/net/openldap23-client/> rehash
|
Установка OpenLDAP сервера
//> cd /usr/ports/net/openldap23-server/
/usr/ports/net/openldap23-server/> make config
|
+--------------------------------------------------------------------+
| Options for openldap-server 2.3.43 |
| +----------------------------------------------------------------+ |
| | [ ] SASL With (Cyrus) SASL2 support | |
| | [ ] PERL With Perl backend | |
| | [ ] SHELL With Shell backend (disables threading) | |
| | [ ] ODBC With SQL backend | |
| | [ ] SLP With SLPv2 (RFC 2608) support | |
| | [ ] SLAPI With Netscape SLAPI plugin API | |
| | [X] TCP_WRAPPERS With tcp wrapper support | |
| | [X] BDB With BerkeleyDB support | |
| | [ ] ACCESSLOG With In-Directory Access Logging overlay| |
| | [ ] AUDITLOG With Audit Logging overlay | |
| | [ ] DENYOP With Deny Operation overlay | |
| | [ ] DYNGROUP With Dynamic Group overlay | |
| | [ ] DYNLIST With Dynamic List overlay | |
| | [ ] LASTMOD With Last Modification overlay | |
| | [ ] PPOLICY With Password Policy overlay | |
| | [ ] PROXYCACHE With Proxy Cache overlay | |
| | [ ] REFINT With Referential Integrity overlay | |
| | [ ] RETCODE With Return Code testing overlay | |
| | [ ] RWM With Rewrite/Remap overlay | |
| | [ ] SYNCPROV With Syncrepl Provider overlay | |
| | [ ] TRANSLUCENT With Translucent Proxy overlay | |
| | [ ] UNIQUE With attribute Uniqueness overlay | |
| | [ ] VALSORT With Value Sorting overlay | |
| | [ ] ACI With per-object ACIs (experimental) | |
| | [X] DYNAMIC_BACKENDS Build dynamic backends | |
| | [X] SLURPD Build slurpd replication daemon | |
+-+------v(+)------------------------------------------------------+-+
| [ OK ] Cancel |
+--------------------------------------------------------------------+
|
/usr/ports/net/openldap23-server/> make install clean
/usr/ports/net/openldap23-server/> rehash
|
Генерируем пароль администратора OpenLDAP командой slappasswd, хеш которого мы ниже добавим в конфиг OpenLDAP
//> slappasswd -s root
New password:*******
Re-enter new password:*******
{SSHA}HaXoFVeJ5HOmvVbFnSB00lCYjIw8N0y+
//>
|
Теперь займемся конфигом OpenLDAP
//> ee /usr/local/etc/openldap/slapd.conf
|
#
# See slapd.conf(5) for details on configuration options.
# This file should NOT be world readable.
#
include /usr/local/etc/openldap/schema/core.schema
include /usr/local/etc/openldap/schema/cosine.schema
include /usr/local/etc/openldap/schema/inetorgperson.schema
include /usr/local/etc/openldap/schema/misc.schema
include /usr/local/etc/openldap/schema/nis.schema
include /usr/local/etc/openldap/schema/openldap.schema
# Define global ACLs to disable default read access.
# Do not enable referrals until AFTER you have a working directory
# service AND an understanding of referrals.
#referral ldap://root.openldap.org
pidfile /var/run/openldap/slapd.pid
argsfile /var/run/openldap/slapd.args
# Load dynamic backend modules:
modulepath /usr/local/libexec/openldap
# moduleload back_bdb
# moduleload back_ldap
moduleload back_ldbm
# moduleload back_passwd
# moduleload back_shell
# Sample security restrictions
# Require integrity protection (prevent hijacking)
# Require 112-bit (3DES or better) encryption for updates
# Require 63-bit encryption for simple bind
# security ssf=1 update_ssf=112 simple_bind=64
# Sample access control policy:
# Root DSE: allow anyone to read it
# Subschema (sub)entry DSE: allow anyone to read it
# Other DSEs:
# Allow self write access
# Allow authenticated users read access
# Allow anonymous users to authenticate
# Directives needed to implement policy:
access to dn.base="" by * read
access to dn.base="cn=Subschema" by * read
access to *
by self write
by users read
by anonymous auth
#
# if no access controls are present, the default policy
# allows anyone and everyone to read anything but restricts
# updates to rootdn. (e.g., "access to * by * read")
#
# rootdn can always read and write EVERYTHING!
#######################################################################
# BDB database definitions
#######################################################################
database ldbm
suffix "dc=mail,dc=local"
rootdn "cn=root,dc=mail,dc=local"
# Cleartext passwords, especially for the rootdn, should
# be avoid. See slappasswd(8) and slapd.conf(5) for details.
# Use of strong authentication encouraged.
rootpw {SSHA}HaXoFVeJ5HOmvVbFnSB00lCYjIw8N0y+
# The database directory MUST exist prior to running slapd AND
# should only be accessible by the slapd and slap tools.
# Mode 700 recommended.
directory /var/db/openldap-data
loglevel 256
# Indices to maintain
index objectClass eq
index cn eq
|
Добавляем в автозагрузку
ldap://127.0.0.1/ - указывем что бы OpenLDAP слушал localhost
ldap://192.168.1.9/ - указывем что бы OpenLDAP слушал Ethernet интерфейс
slapd_enable="YES"
## Этот параметр пишите в одну строку без переноса "\"
slapd_flags='-h "ldapi://%2fvar%2frun%2fopenldap%2fldapi/ ldap://127.0.0.1/ \
ldap://192.168.1.9/"'
########
slapd_sockets="/var/run/openldap/ldapi"
|
Запускаем OpenLDAP
//> /usr/local/etc/rc.d/slapd start
Starting slapd.
//>
|
Проверяем работает ли он
//> ps axw | grep openldap
|
1729 ?? Ss 0:00,02 /usr/local/libexec/slapd -h
ldapi://%2fvar%2frun%2fopenldap%2fldapi/ ldap://127.0.0.1/
ldap://192.168.1.9/ -u ldap -g ldap
1780 p0 R+ 0:00,00 grep openldap
|
//> netstat -nap tcp | grep 389
|
tcp4 0 0 192.168.1.9.389 *.* LISTEN
tcp4 0 0 127.0.0.1.389 *.* LISTEN
|
Создаем КОРЕНЬ
//> ee /var/db/openldap-data/base.ldif
|
dn: dc=mail, dc=local
objectClass: dcObject
objectClass: organization
objectClass: top
dc: mail
o: mail
| Добавим схему в OpenLDAP
/var/db/openldap-data/>ldapadd -x -D "cn=root,dc=mail,dc=local" \
-h 192.168.1.9 -W -f base.ldif
Enter LDAP Password:
adding new entry "dc=mail, dc=local"
/var/db/openldap-data/>
|
//> cd /usr/ports/net/phpldapadmin
/usr/ports/net/phpldapadmin/> make install clean
/usr/ports/net/phpldapadmin/> rehash
|
Добавляем алиас в апач
//> ee /usr/local/etc/apache/httpd.conf
|
Alias /phpldapadmin "/usr/local/www/phpldapadmin/htdocs/"
<Directory "/usr/local/www/phpldapadmin/htdocs">
Options none
AllowOverride none
Order Deny,Allow
Deny from all
Allow from 127.0.0.1 192.168.1.0/24 .domain.local
</Directory>
|
Слегка правим конфиг
//> ee /usr/local/www/phpldapadmin/config/config.php
|
$ldapservers->SetValue($i,'server','host','127.0.0.1');
|
Создание адресной книги

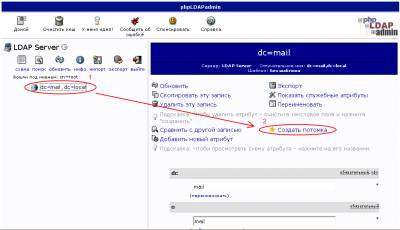

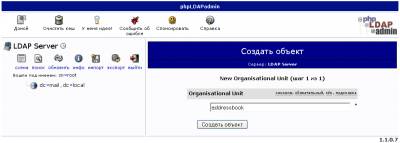

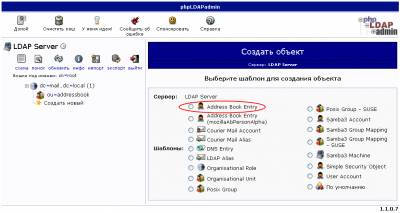
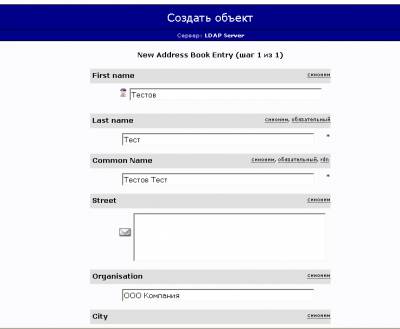
Источник: http://www.lissyara.su/?id=1938 | 
 Каталог статей
Каталог статей Регистрация
Регистрация Вход
Вход














